Double up on security by protecting your applications and environments with two-factor authentication (2FA). It's the simplest, most effective way to verify that your users are who they say they are.
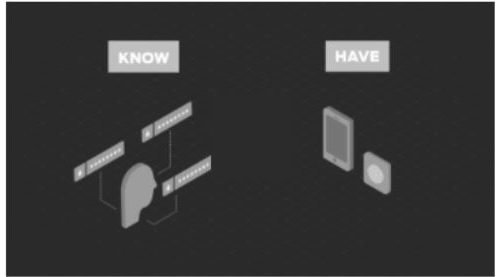
Two-factor authentication (2FA) is a specific type of multi-factor authentication (MFA) that strengthens access security by requiring two methods (also referred to as authentication factors) to verify your identity. These factors can include something you know - like a username and password - plus something you have - like a smartphOne app - to approve authentication requests.
2FA protects against phishing, social engineering and password brute-force attacks and secures your logins from attackers exploiting weak or stolen credentials.
Two-factor authentication (2FA) is the foundational element of a zero trust security model. In order to protect sensitive data. You must verify that the users trying to access that data are who they say they are. 2FA is an effective way to protect against many security threats tnat target user passwords and accounts. suchas phishing, brute-force attacks, credential exploitation and more.
Let's say you use a usernarne and password to complete primary authentication to an application. That information is sent over the Internet (your primary network). You'll want to use a different (out-of-band) channel to complete your second factor. Approving a push notification sent over your mobile network is an example of out-of-band authentication.
So why does it matter? If a remote attacker is able to tap into your computer via your Internet connection, they can steal your password, and your second form of authentication - if both are delivered over the same channel.
Without your physical device, remote attackers can't pretend to be you in order to gain unauthorized access to corporate networKs, cloud storage, financial information, etc. stored in applications.
By integrating two-factor authentication with your applications, attackers are unable to access your accounts without possessing your physical device needed to complete the second factor.
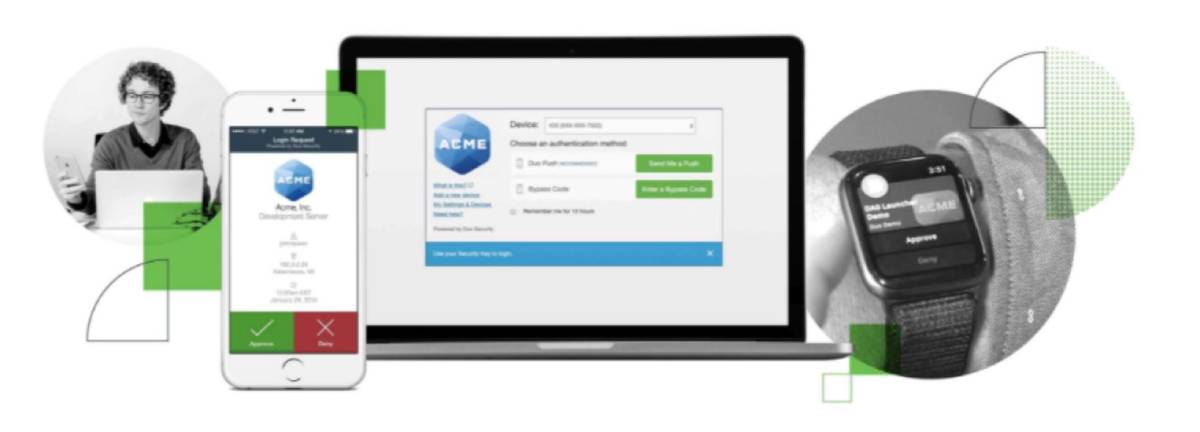
We know the most effective security solution is one your users actually use.
2FA solution only requires your users to carry one device - their smartphone, with the Duo Mobile app installed on it. Duo Mobile is available for both iPhones and Android, as well as wearables like the Apple Watch.
With support for a large array of authentication methods, logging in via push notification is fast and easy with Duo Mobile. We strongly recommend using Duo Push or U2F as your second factor, because they're most secure and can protect against man-in-the-middle (MITM) attacks, but with Duo's flexibility and customizability, you'll be able to find the adaptive authentication method tnat meets the unique needs of your diverse user base.
Duo integrates to protect every point of access, from on-premises, to webbased, to cloud-based applications. Deployment is quick and easy, and the platform's user-friendly authentication experience and intuitive administrator dashboard make managing your security protocols a breeze.
Duo puts your organization on the fast-track to zero trust by securing the modem workforce. The simple, all-inone platform lets you verify user identities, assess and act on the health of devices, set adaptive access policies, and protect users' productivity with modem remote access and SSO capabilities. Learn more about Duo's approach to zero trust here.
At Duo, we believe every organization should have a 2FA solution, so we take pride in providing a simple, yet scalable, security platform that works. With three editions and a host of capabilities built in, you can choose the solution tnat's just perfect for your business. See editions and pricing here.
Need more information to get up to speed on 2FA basics and security industry terminology? We're here to help. Below, you'll find answers to your questions and resources to help you take the next steps toward a more secure workforce.
Factors are the pieces of information a user can provide to verify their identity. 2FA is the most commonly used, but there are, in fact, five factors of authentication used by security professionals today.
The Knowledge factor verifies identity by requesting information only an individual user would know. The most common example of a knowledge factor of authentication is a password. A user's password should be private only to them, allowing them to use it as a methOd to confirm their identity.
Possession factors verify the identity of a user by requiring proof of information that only the user should possess. Tokens are a commonly used possession factor of authentication. These tokens generate a rotating passcode that users must physically carry on their person.
Duo Mobile combines the knowledge factor and possession factor of authentication to create the world's most trusted 2FA platform. Two other possession factors of authentication are HMAC-based One-time Password (HOTP) and Time-based One-time Password (TOTP). Both authentication methods generate temporary passwords from a physical device carried by the user. HOTP tokens expire once they are used while TOTP tokens expire if not used within thirty seconds.
lnherence factors of authentication verify the identity of a user by using attributes that would belong only to that user. Fingerprint scanning is the most obvious inherence factor used today.
Fingerprints are unique to individuals, so many organizations use them as a way to confirm who their users are. In addition to fingerprints, there are many other inherence factors used today: voice. handprints, face recognition, and more.
Location factors of authentication confirm the identity of a user based on their location in the world. If a user had registered an account in one country, for example, and suddenly there are login attempts from another, location factors could trigger and attempt to verify the identity of the new user. Many location factors are based on the IP address of the original user and compares the address to that of the new attempt to access information.
Time factors of authentication verify the identity of a user by challenging the time of the access attempt This is based on the assumption that certain behaviors (like logging into a work computer) should happen within predictable time ranges. If an attempt to access a platform happens outside of the usual time range, the attempt can be challenged or terminated until a user can verify their identity.
The need for two-factor authentication has increased as companies, governments, and the public realize that passwords alone are not secure enough to protect user accounts in the current technical landscape. In fact, the average cost of data breaches today is over two trillion dollars annually. While 2FA protects against a multitude of threats, the most common threats include:
A traditional password can be used by anybody who gets their hands on it. If a user writes down their password on a pad of paper, for example, that password can be stolen to gain access to an account. 2FA, by contrast, validates the user with a second device after a password is entered.
Hackers will often send emails that include links to malicious websites designed to either infect a user's computer or convince them to enter their passwords. Once obtained, a password can be used by whoever manages the hacking attempt. 2FA fights phishing by adding a second layer of validation after the password has been entered.
Hackers will often simply manipulate users into giving up their passwords. By posing as an IT professional at the user's company, they can earn the trust of the user before asking for login credentials. 2FA protects against this by validating the location and IP of every login attempt after a password has been entered.
In a brute-force attack, a hacker randomly generates passwords for a specific computer until they land on the correct sequence. 2FA's second layer of protection requires a login attempt to be validated before granting access.
Even if a user hasn't written down their password, hackers can use malware to track and copy a user's password as they type. Hackers track every keystroke and store the password to be used later. The second layer of validation in 2FA lets a user ensure that the login attempt is their own, even if their password has been compromised.